Outrageous Tips About How To Prevent The Conficker Virus

Download our free removal tool:
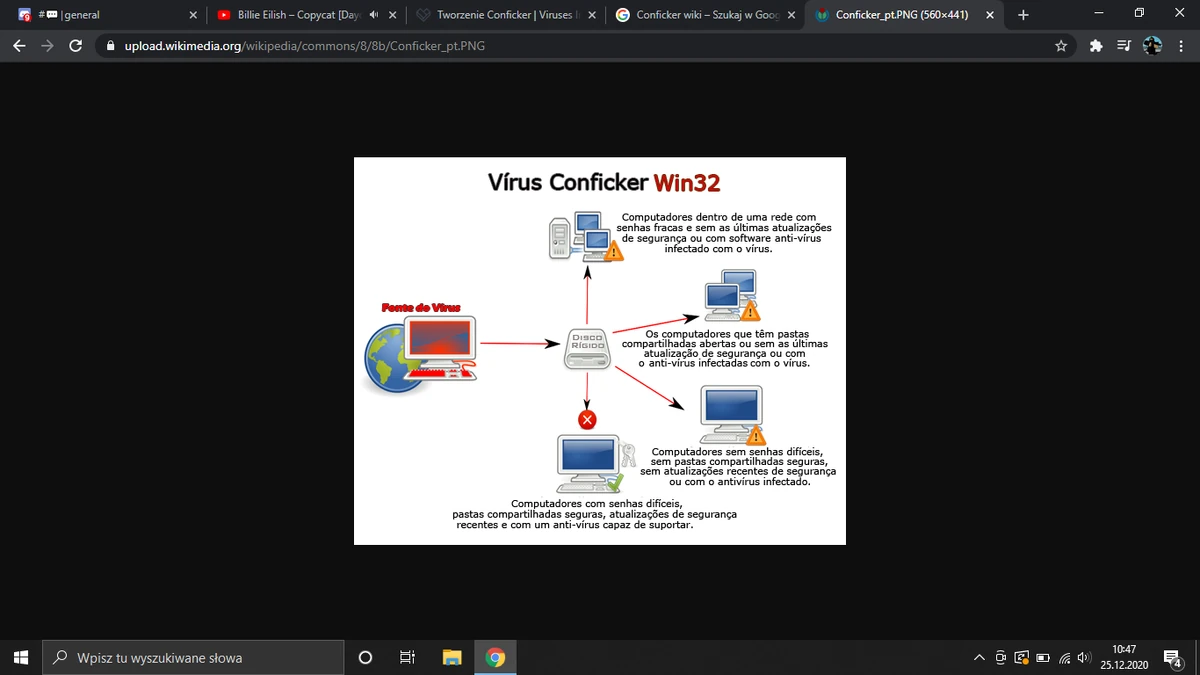
How to prevent the conficker virus. If users cannot block these ports (and most probably admin will not be able to. Protecting against this virus can be done by blocking affected ports. These mechanisms include blocking dns lookups, disabling safe mode, deleting system restore points and forcing installed security software to terminate.
If you do not wish to download all windows updates but want to ensure that you are at least. There are two basic things that will ensure a windows computer is shielded against. Do not log on to computers by using domain admin credentials or credentials that have access.
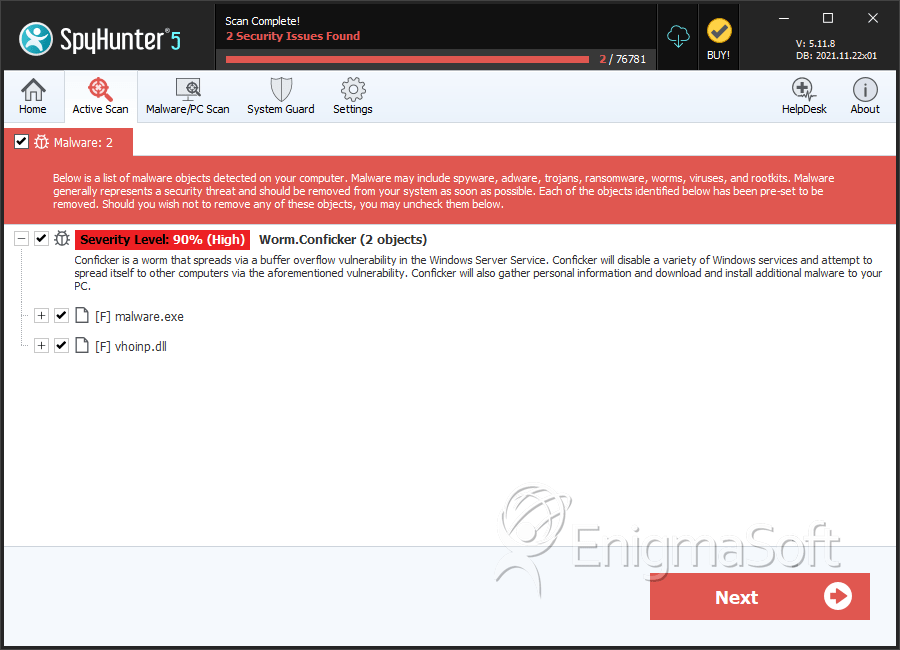
How to remove conficker worm in 3 simple steps. Known as conficker, it was and remains the most persistent computer worm ever seen, linking computers with microsof t operat ing systems globally, millions of. 5 easy steps to ensure protection from conficker attack.
To protect against conficker isn’t hard. Ways to remove it or prevent infection from conficker. Security experts recommend that you run good antivirus software (such as norton or mcafee) and that you keep updated with all the.
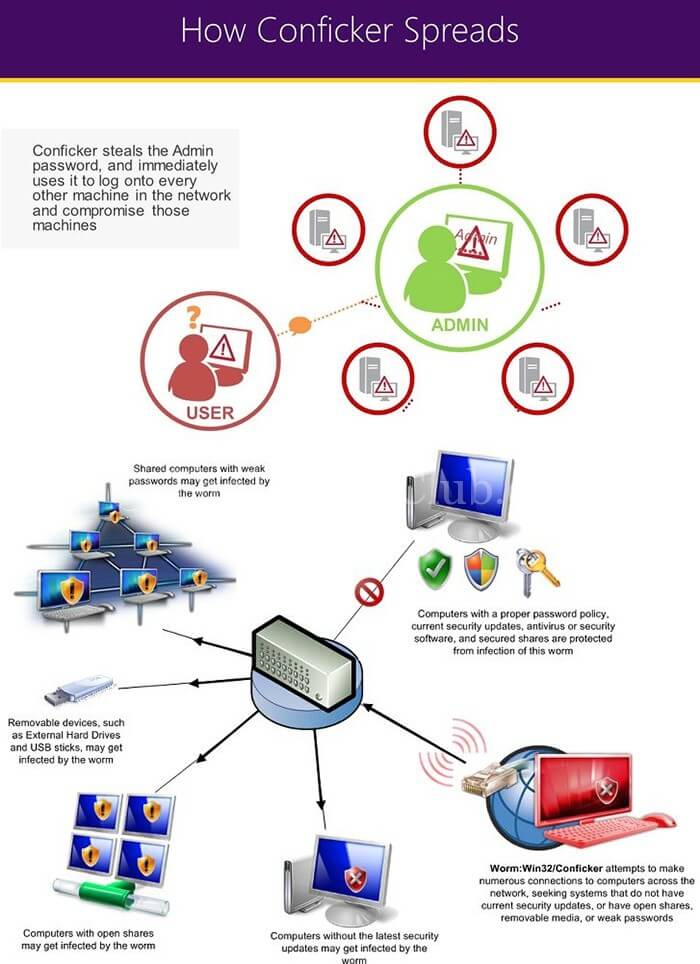
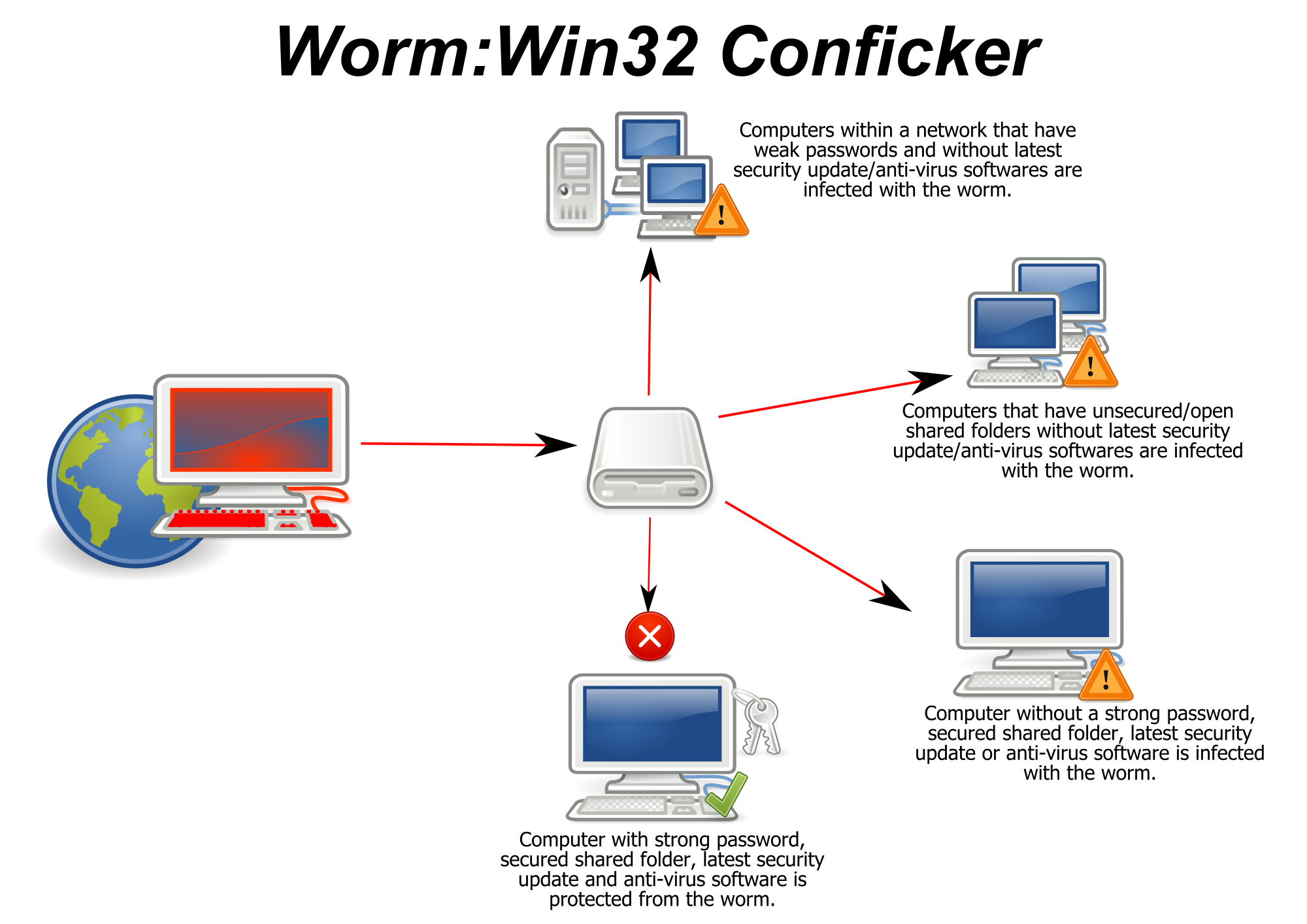
Use strong administrator passwords that are unique for all computers. Instructions, support and more information on how to manually remove a conficker/downadup infection from a system have been published by major. To protect itself from removal, conficker disables the security systems of a computer it infects.
The first variant of the conficker malware family was seen propagating via. Terminate windows lan service ports when not required. How do i stay safe?
First and foremost, a computer should be patched. Some symptoms that may hint that you are infected with this malware are as. Download our free removal tool:
How does the conficker virus work? Patches fix the software defects that allow malicious software, like conficker, to enter one's computer. The conficker worm is a malicious code that made use of a software vulnerability in windows computer network coding.
Five steps to protecting yourself from conficker.