Outrageous Tips About How To Prepare For Conficker Virus
Published mar 27, 2009.
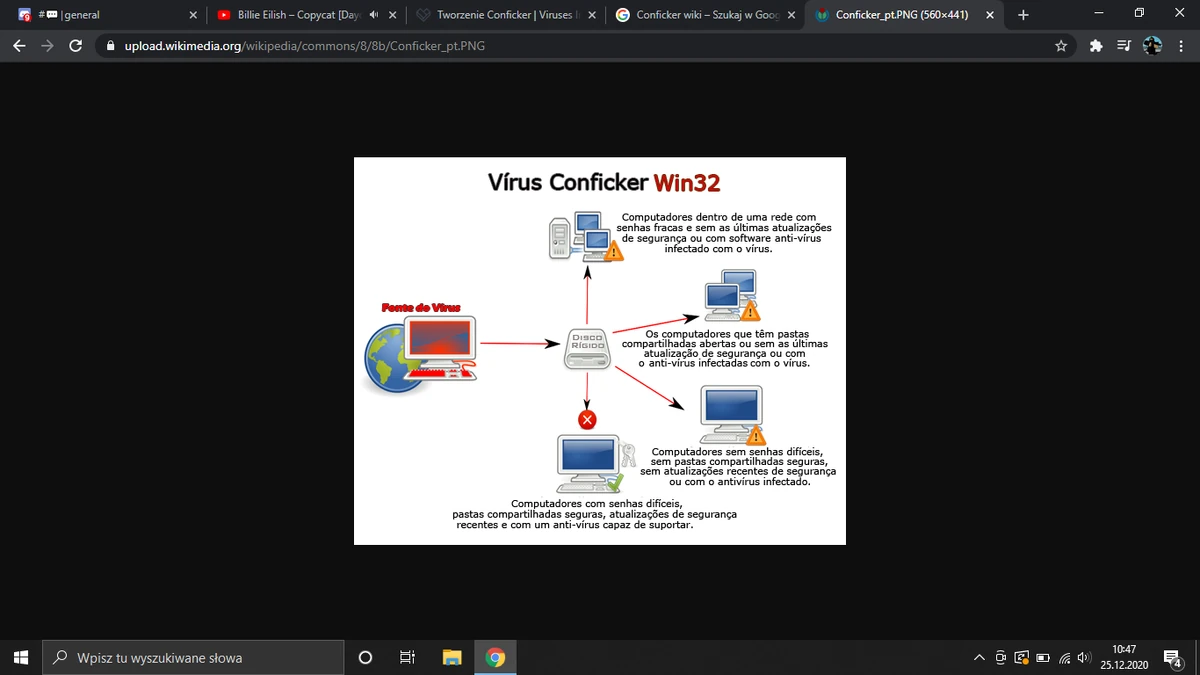
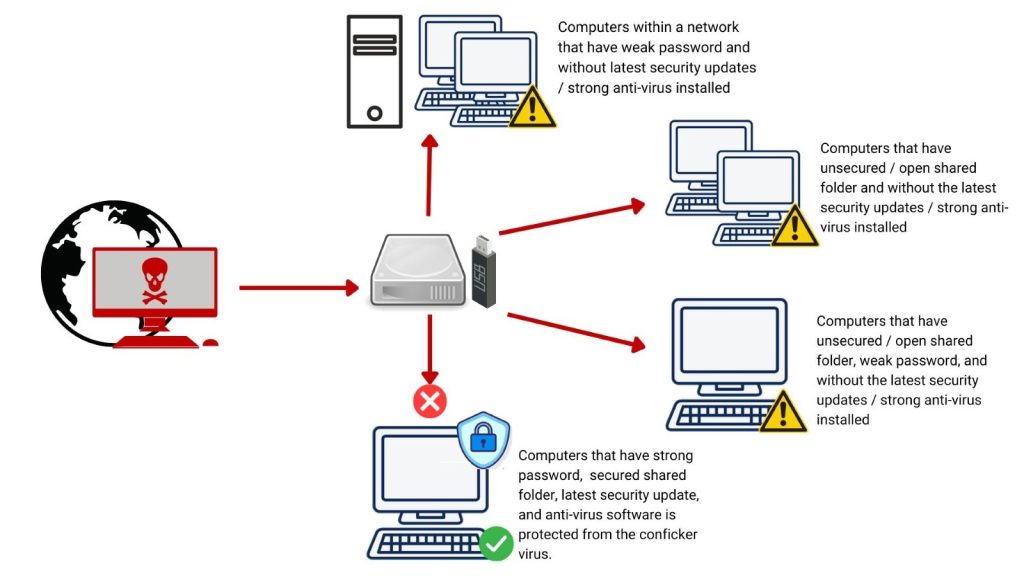
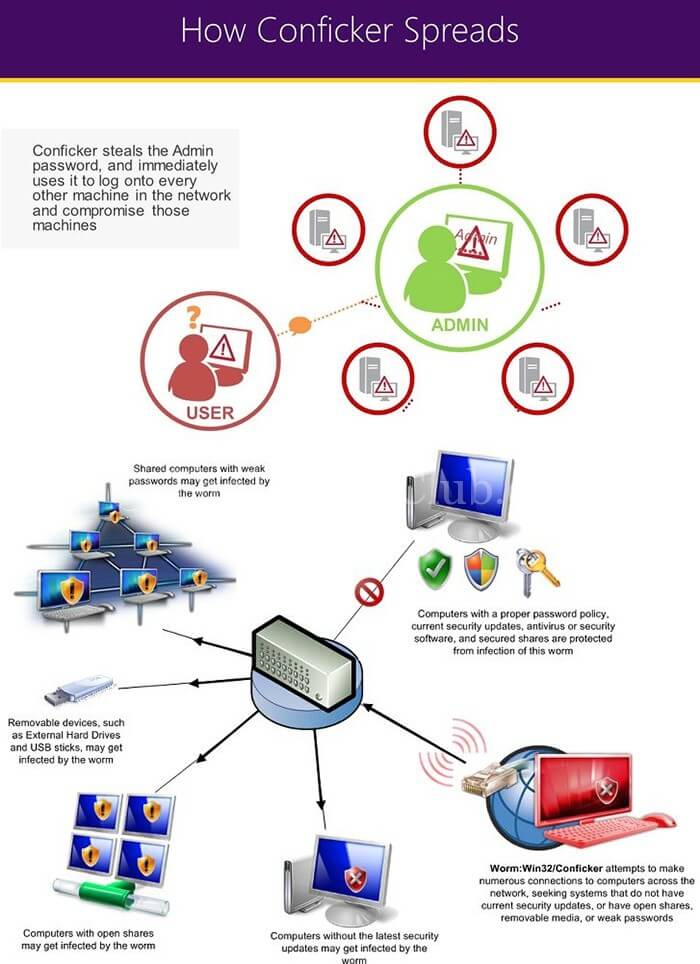
How to prepare for conficker virus. The conficker worm is a malicious code that made use of a software vulnerability in windows computer network coding. How to remove conficker worm in 3 simple steps. Download and install wireshark on a computer that is constantly getting dropped on by a conficker infected computer.
A free trial version of these should. It was deemed one of the scariest malware to hit the past decade, and yet. If you can't get there, the chances are you've been infected:
We suggest to scan for and disinfect conficker machines as soon as possible, regardless of speculations about. Start the logging within wireshark. How does the conficker virus work?
Conficker malware writers made use of domain names rather than ip addresses to make their attack networks resilient against detection and takedown. If you do not wish to download all windows updates but want to ensure that you are at least. You can download the msrt.
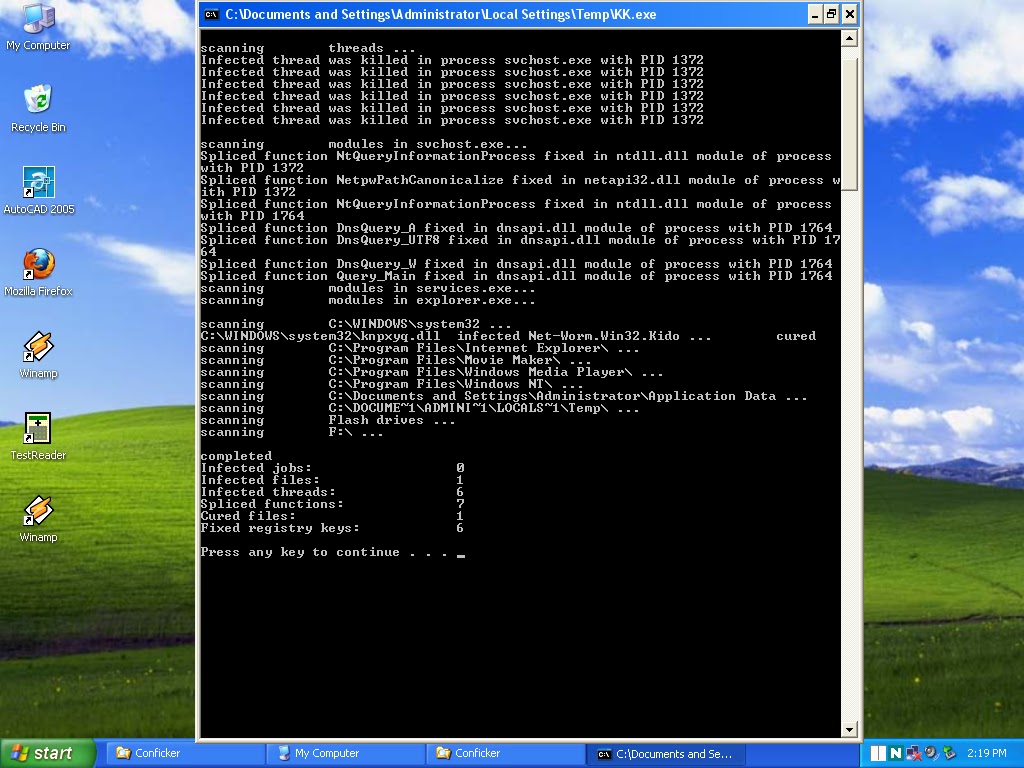
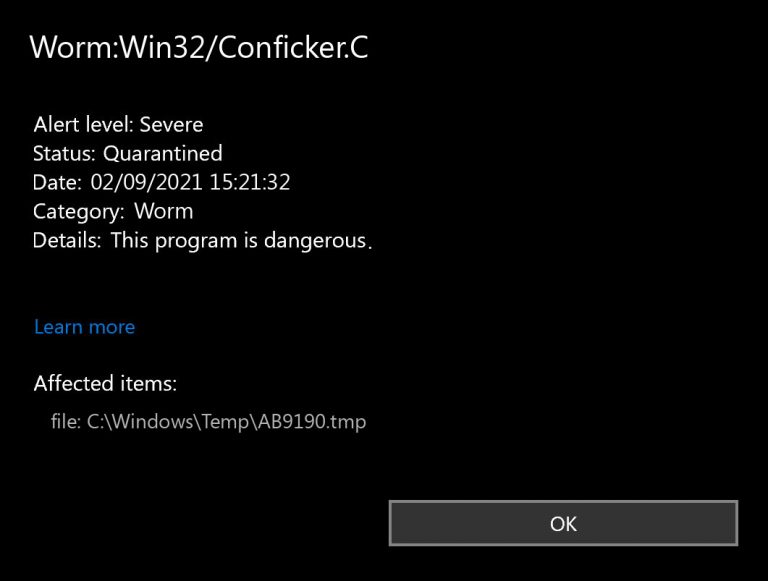
Microsoft help and support have provided a detailed guide to removing a conficker infection from an infected pc, either manually or by using the malicious. Conficker.c (also known as kido or downadup) is the third iteration of a worm which first began slithering. The best way to find out whether you already have conficker is to use one of the microsoft, symantec or mcafee security tools.
If it is infected, what is the best course of action? Known as conficker, it was and remains the most persistent computer worm ever seen, linking computers with microsof t operat ing systems globally, millions of. For longevity alone, a big contender must be conficker, a windows worm that still registers 150,000 infections per.
Conficker is designed to communicate with its controllers by trying to connect to hundreds of different internet domain names each day: Conficker, also known as downup, downadup and kido, is a computer worm targeting the microsoft windows operating system that was first detected in november 2008. Protecting against this virus can be done by blocking affected ports.
Some symptoms that may hint that you are infected with this malware are as. Scan the infected computer's network for vulnerable computers and try to infect them. Proofpoint honours top australian partners.
Download our free removal tool: